Beyond the Basics: Building an Impenetrable Mobile App in 2025
A mobile app is more than a utility; it’s a direct gateway to sensitive user data and a core pillar of your brand’s trustworthiness. The consequences of a security breach are severe, extending beyond financial penalties to cause catastrophic reputational damage and permanently erode user confidence. Standard security protocols are no longer adequate against determined adversaries.
The modern threat environment demands a proactive, multi-layered defense strategy embedded throughout the entire development lifecycle. This comprehensive mobile app security checklist provides a deep, actionable framework for building a genuinely secure application. It moves far beyond surface-level advice to offer specific, implementation-focused guidance. We will explore the fundamental pillars of mobile security, from robust data encryption and secure authentication to advanced anti-tampering techniques and rigorous vulnerability testing.
However, building a secure app is only the first step. Maintaining that security requires the agility to respond to threats in real-time. A critical, often-overlooked aspect of a sustained security posture is the ability to deploy urgent patches instantly. This is where secure Over-The-Air (OTA) update platforms become indispensable. Tools like CodePushGo enable developers to bypass slow app store review cycles, delivering encrypted security fixes directly to user devices and ensuring protection is never delayed. This list will equip your team with the knowledge to not only build securely but also to maintain that security posture with confidence.
1. Data Encryption in Transit and at Rest
Data encryption is a fundamental security practice that protects information in its two primary states: when it is moving between the app and a server (in transit) and when it is stored on a device or backend (at rest). This process transforms readable data into an unreadable format using an algorithm, ensuring that even if the data is intercepted or a device is compromised, the information remains confidential without the correct decryption key. Its implementation is a non-negotiable baseline for any secure application and is often a strict requirement for compliance with regulations like GDPR and HIPAA.

Implementing Encryption in Transit
Data being transmitted over a network, especially public Wi-Fi, is highly susceptible to man-in-the-middle (MitM) attacks. An attacker can position themselves between the app and the server to eavesdrop on or even modify the communication.
- Mandate Modern TLS: All communication between the mobile app and its backend servers must be forced over HTTPS and secured with a modern cryptographic protocol like TLS 1.2 or TLS 1.3. Critically, you must configure your server to reject connections using outdated and vulnerable protocols like SSL.
- Use Certificate Pinning: To defend against sophisticated MitM attacks that use fraudulent certificates, implement certificate pinning. This technique hardcodes the server’s legitimate SSL/TLS certificate identity directly into the mobile app. When the app initiates a connection, it verifies that the server’s certificate matches the pinned one, preventing attackers from impersonating your server even if they compromise a Certificate Authority (CA).
Securing Data at Rest
Data at rest includes all sensitive information stored persistently on the user’s device or your servers, such as user credentials, personal information, and application settings. This data is vulnerable to physical device theft, malware attacks, and unauthorized filesystem access. Any robust mobile app security checklist must prioritize its protection.
- Leverage Platform-Specific Secure Storage: For sensitive data like authentication tokens, API keys, and passwords, always use the platform’s native secure storage mechanisms. The iOS Keychain and Android Keystore system are designed to store these secrets in a hardware-backed, encrypted enclave, making them extremely difficult to extract.
- Encrypt Databases and Files: For application-specific data stored in local databases (like SQLite) or files, apply an additional layer of encryption. Libraries such as SQLCipher offer transparent, full-database AES-256 encryption, a standard practice in banking apps like Chase Mobile.
- Practice Strong Key Management: Your encryption is only as strong as your key management. Never hardcode encryption keys or store them in plaintext within the app’s code or insecure storage. Use a strong Key Derivation Function (KDF) like Argon2 to generate keys from user input, or manage keys securely using the Keystore/Keychain. Implementations like the Signal Protocol, popularized by Open Whisper Systems, provide a gold standard for secure key exchange and management.
2. Secure Authentication and Authorization
Secure authentication and authorization are the cornerstones of application access control. Authentication is the process of verifying a user’s identity, while authorization determines what an authenticated user is permitted to do. A failure in either can lead to unauthorized data access, privilege escalation, and complete account takeovers. Implementing these controls correctly is a non-negotiable step in any comprehensive mobile app security checklist and is fundamental to building user trust.

Strengthening Authentication
Verifying that users are who they claim to be is the first line of defense. Modern applications must move beyond simple password-based systems, which are notoriously weak and susceptible to brute-force or credential-stuffing attacks.
- Implement Multi-Factor Authentication (MFA): Add a critical layer of security by requiring two or more verification methods. This can include something the user knows (password), something the user has (a phone with an authenticator app like Google Authenticator), or something the user is (biometrics). Platforms like Duo Security and Okta provide robust MFA solutions.
- Leverage Biometrics Securely: Use native platform APIs like Apple’s Face ID/Touch ID and Android’s BiometricPrompt API. These frameworks, standardized by organizations like the FIDO Alliance, handle the sensitive biometric data within a secure hardware enclave on the device, meaning your app never directly accesses it.
Enforcing Authorization and Session Management
Once a user is authenticated, their access must be strictly controlled throughout their session. This prevents authenticated users from accessing data or functions they shouldn’t. Understanding these modern app security standards is crucial for a secure implementation.
- Adopt the Principle of Least Privilege (PoLP): Grant users the minimum level of access required to perform their tasks. Authorization logic should be enforced on the backend, never trusting the client-side app to make security decisions.
- Secure Session Tokens: For apps using OAuth 2.0, you must implement the Proof Key for Code Exchange (PKCE) extension. This is a critical defense against authorization code interception attacks in public clients like mobile apps.
- Practice Secure Token Handling: Always store session tokens and refresh tokens in the platform’s secure storage: the iOS Keychain or Android Keystore. Enforce reasonable session timeouts based on the app’s sensitivity and ensure the logout function invalidates the token on the server, not just clears it from the device.
3. Input Validation and Sanitization
Any data entering your app from an external source, whether from a user or another API, is a potential attack vector. Input validation and sanitization is a defensive security measure that involves rigorously filtering all incoming data to ensure it is safe and conforms to expected formats. This process, championed by security leaders like OWASP and Microsoft, is the primary defense against devastating vulnerabilities like SQL injection and Cross-Site Scripting (XSS), where malicious input is executed by the application. In a banking app, this means strictly validating account numbers; in an e-commerce app, it means sanitizing every product review to remove malicious scripts.
This concept map illustrates the core relationship between the central principle of Input Validation and Sanitization and three critical defensive techniques: Whitelist Validation, Parameterized Queries, and Output Encoding.
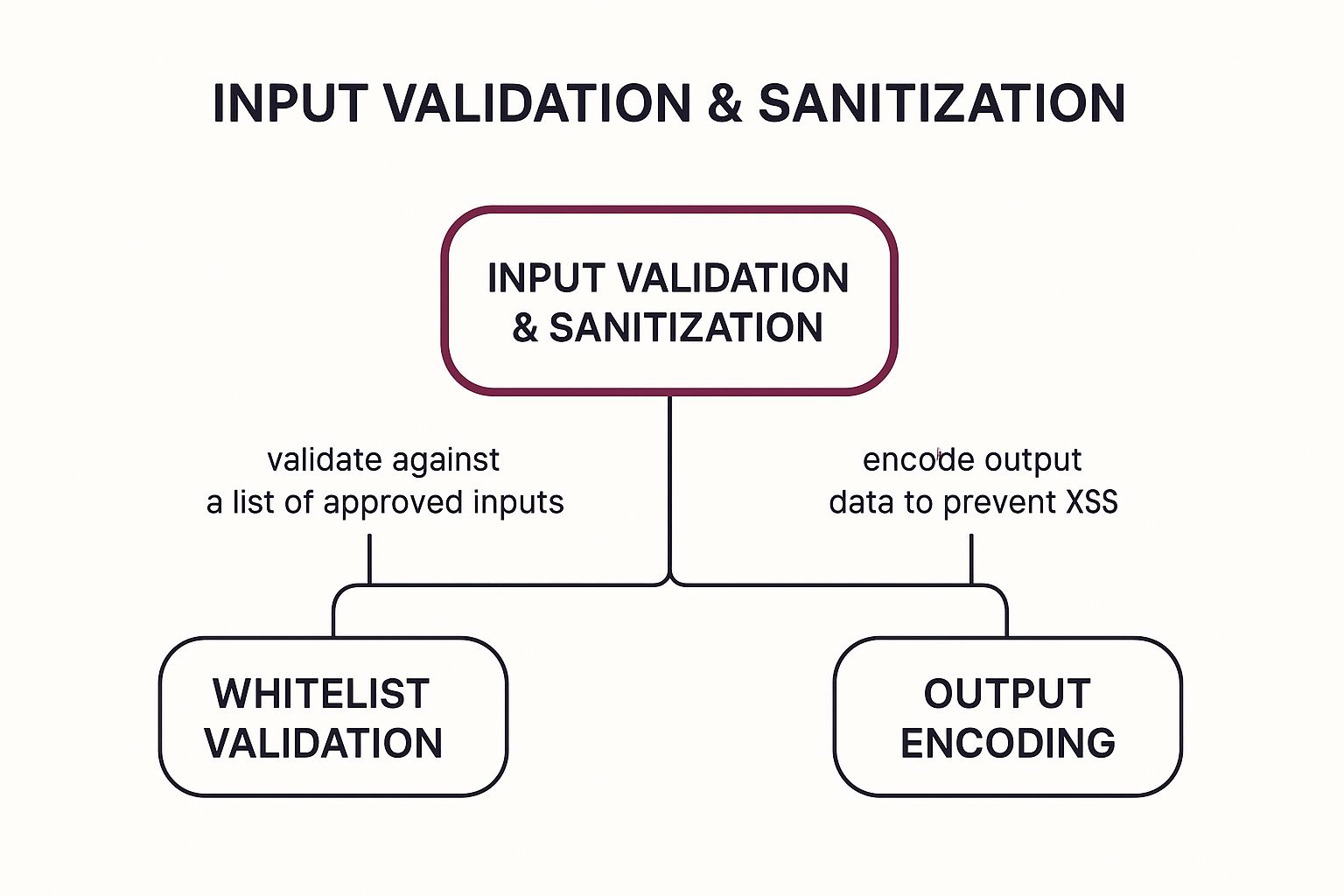 The visualization highlights how these three pillars work together, creating a layered defense that ensures data is safe from its entry point through to its processing and final display.
The visualization highlights how these three pillars work together, creating a layered defense that ensures data is safe from its entry point through to its processing and final display.
Implementing Proactive Validation Rules
The goal of validation is to define and enforce strict rules for what data is acceptable. A proactive, explicit approach is always superior to a reactive one. A robust mobile app security checklist must mandate these rules be enforced without compromise.
- Implement Whitelist Validation: Instead of trying to block known-bad inputs (blacklisting), which is brittle and easily bypassed, exclusively allow known-good inputs (whitelisting). For example, a field for a state abbreviation should only accept a predefined list of two-letter codes, rejecting everything else.
- Validate on Both Client and Server: Client-side validation provides immediate feedback and improves the user experience, but it can be easily bypassed by an attacker. Therefore, you must always duplicate and enforce all validation logic on the server-side, which acts as the ultimate source of truth.
Neutralizing Malicious Payloads
Even if data appears to be in the correct format, it may contain malicious payloads designed to be executed by a backend system or another user’s browser. Sanitization and proper data handling are essential to neutralize these threats.
- Use Parameterized Queries: To prevent SQL injection, never build database queries by concatenating strings with user input. Instead, use parameterized queries (also known as prepared statements). This technique ensures that user input is always treated as data, not as executable code, completely neutralizing this attack vector.
- Encode Output Data: To prevent XSS attacks in social media feeds or product reviews, you must encode all data before displaying it in the UI. Output encoding converts potentially dangerous characters like
<and>into their harmless HTML entity equivalents (<and>), ensuring they are rendered as text instead of being executed as code by a browser. - Implement Secure Error Handling: Ensure that application error messages are generic. Never reveal sensitive system details like stack traces, database versions, or file paths, as this information provides attackers with a roadmap for further exploitation. You can explore more advanced security strategies to build a comprehensive defense.
4. Secure Code Storage and Anti-Tampering
Once an application is compiled and deployed, its binary code becomes a direct target for attackers. They can use reverse engineering tools to decompile the app, exposing your source code, proprietary algorithms, and embedded API keys. This knowledge can be used to discover vulnerabilities, steal intellectual property, or create tampered, malicious versions of your app. Secure code storage and anti-tampering techniques are designed to actively defend against these threats by making the application an inhospitable environment for attackers. Including these measures is a vital step in any comprehensive mobile app security checklist.
Protecting Code from Reverse Engineering
The primary goal here is to make your application’s logic as difficult to understand as possible, even if an attacker manages to decompile it. This significantly raises the cost and effort required for an attack, often deterring all but the most determined adversaries.
- Implement Code Obfuscation: This is a process of transforming the app’s code into a functionally identical but difficult-to-read version. Tools like Guardsquare’s ProGuard (for Java) and DexGuard (for Android) automatically rename classes, methods, and variables into meaningless characters, strip metadata, and encrypt strings, making the decompiled code a tangled mess for a human analyst.
- Use Anti-Debugging Techniques: An application can be designed to detect when a debugger is attached to its process. Upon detection, the app can immediately terminate, enter a broken state, or silently alert your backend servers. This thwarts an attacker’s ability to step through the code line-by-line to analyze its behavior and manipulate memory.
Implementing Runtime Application Self-Protection (RASP)
RASP enables an application to monitor its own state and the environment it is running in, allowing it to detect and respond to attacks in real time. This is a dynamic defense mechanism that goes beyond static code protection, acting as an immune system for your app.
- Perform Integrity Checks: At runtime, the app can calculate its own checksum or validate its code signature and compare it to a securely stored original value. If there’s a mismatch, it indicates the application package has been modified or repackaged. High-security apps, like those in mobile banking, use this to immediately shut down and prevent execution. You can explore a variety of secure development practices that complement these checks.
- Detect Compromised Environments: Apps can check if they are running on a rooted (Android) or jailbroken (iOS) device. Since these environments grant attackers elevated privileges, the app can respond by limiting functionality, a concept known as graceful degradation. For example, a DRM-protected media app might still stream content but disable offline downloads on a jailbroken phone.
- Combine and Update Defenses: No single technique is foolproof. A robust strategy, used by leaders like Arxan Technologies and Verimatrix, involves layering obfuscation, anti-debugging, and RASP. Furthermore, these protections must be regularly updated, as attackers are constantly developing new tools and bypass methods.
5. Secure Network Communication
Secure network communication involves all measures taken to protect data transmitted between the mobile application and its backend services. This is a critical defense against network-based attacks like eavesdropping and man-in-the-middle (MitM) interception, which are especially prevalent on public or untrusted Wi-Fi networks. Failing to secure this channel renders other security measures, like on-device encryption, ineffective as data can be stolen in transit. A robust plan for network security is therefore an essential pillar of any mobile app security checklist.
Enforcing Secure Transport Layer Protocols
The foundation of secure communication rests on establishing a private, authenticated channel. Modern mobile operating systems provide frameworks to enforce this, but developers must configure them correctly to prevent vulnerabilities. This involves more than just using HTTPS; it requires a strict and modern configuration.
- Mandate Modern TLS: All communication must be forced over HTTPS and secured with a modern protocol like TLS 1.2 or TLS 1.3. Explicitly configure your server and app to reject connections using outdated and insecure protocols like SSL. Tools like Apple’s App Transport Security (ATS) and Android’s Network Security Configuration file allow you to define these rules declaratively.
- Implement Certificate Pinning: To defend against sophisticated MitM attacks that use fraudulent certificates, implement certificate pinning. This technique, famously used by companies like Twitter, hardcodes the server’s legitimate SSL/TLS certificate identity into the app. Always include backup pins to ensure smooth certificate rotations without locking users out.
- Validate the Entire Certificate Chain: Ensure your app validates not just the server’s leaf certificate but the entire chain up to a trusted root Certificate Authority (CA). This prevents attacks where an intermediate certificate is compromised.
Securing API Endpoints and Data Exchange
A secure TLS tunnel is necessary but not sufficient. The protocols and data formats used for communication within that tunnel must also be secure to protect against application-level attacks. The security of your API directly impacts the security of your mobile app.
- Use Strong Authentication Protocols: Authenticate and authorize API requests using robust, industry-standard protocols. Frameworks like OAuth 2.0 are ideal for managing authorization, while JSON Web Tokens (JWTs) provide a stateless and secure way to transmit user identity and permissions for each request.
- Implement Proper Network Error Handling: Network connections can and will fail. Your app must handle these failures gracefully without leaking sensitive information. Error messages sent to the user should be generic and never expose internal server details, stack traces, or database errors.
- Consider API Gateway Security: Placing an API gateway between your app and your backend microservices can centralize security enforcement. It can handle rate limiting, authentication, and request validation, providing a consistent security layer for all your backend services, a strategy seen in the architectures of companies like Netflix and Uber.
6. Sensitive Data Protection and Privacy
Beyond just encrypting data, a robust security strategy involves a deep commitment to protecting sensitive user information throughout its entire lifecycle. This means mindfully identifying, classifying, handling, and minimizing the data your app collects, processes, and stores. In an era defined by regulations like GDPR and CCPA and user-centric privacy features like Apple’s App Tracking Transparency, building user trust is as critical as preventing a technical breach. A proactive approach to privacy is therefore an essential pillar of any complete mobile app security checklist.
Proactive Data Mapping and Minimization
Before you can protect data, you must understand it. The first step is to create a comprehensive map of all user data your application interacts with, from collection points in the UI to storage on the device and backend servers. This process illuminates how data flows through your system, who has access to it, and where it is ultimately stored or deleted. This knowledge is fundamental to practicing data minimization, a core privacy principle.
- Conduct a Data Mapping Audit: Systematically document every piece of personal data you collect (e.g., name, email, location, device ID). Trace its journey through your app and backend to identify all points of use, storage, and transmission. This audit reveals potential risks and unnecessary data collection.
- Embrace Data Minimization: Adhere to the principle of collecting only the data that is absolutely essential for the app’s core functionality. If a feature can work without access to a user’s contacts, don’t ask for that permission. This reduces your app’s attack surface and compliance burden.
- Use Privacy-Enhancing Technologies: For analytics and data processing, consider techniques like differential privacy. This method adds statistical noise to datasets, allowing you to gather valuable insights without compromising the privacy of any single individual.
Implementing User-Centric Privacy Controls
Modern users expect and regulations demand transparent control over personal data. Your app must empower users with clear, accessible, and granular privacy settings. This not only builds trust but is a legal requirement in many jurisdictions. Frameworks like Apple’s App Tracking Transparency and Google’s Privacy Sandbox are leading examples of the industry’s shift towards user empowerment.
- Provide Granular Controls: Avoid bundling all permissions into a single “accept” button. Allow users to enable or disable specific data-sharing permissions, such as location access, contact syncing, or push notifications, individually.
- Offer Data Portability and Deletion: As mandated by GDPR and CCPA, you must provide users with an easy way to download their data and a straightforward mechanism to request the permanent deletion of their account and associated information.
- Be Transparent with Just-in-Time Notices: Instead of a long, dense privacy policy at startup, explain why you need a specific permission at the exact moment you ask for it. For example, explain “We need your location to show you nearby stores” right before the OS-level permission prompt appears. For a deeper dive into these regulatory and practical aspects, exploring resources on sensitive data protection strategies can provide further clarity.
7. Security Testing and Vulnerability Assessment
Security testing is a systematic process of evaluating your mobile application to identify and remediate security vulnerabilities before they can be exploited. This proactive approach involves a combination of automated and manual techniques to probe the app for weaknesses, from insecure data storage to flawed business logic. Making this a core part of your development lifecycle is essential for building trust and protecting users, transforming security from an afterthought into an integral quality gate. A robust mobile app security checklist must include continuous testing to be effective against evolving threats.
Key Testing Methodologies
A comprehensive security testing strategy does not rely on a single method. Instead, it layers multiple approaches to cover the application from different angles, analyzing both its internal structure and external behavior.
- Static Application Security Testing (SAST): This “white-box” testing method analyzes the application’s source code, bytecode, or binary without executing it. SAST tools like Checkmarx and Veracode are excellent for identifying vulnerabilities early in the development cycle, such as hardcoded secrets, insecure API usage, and weak cryptographic implementations.
- Dynamic Application Security Testing (DAST): This “black-box” approach tests the app in its running state. DAST tools, such as OWASP ZAP, simulate attacks against a live application to find runtime vulnerabilities like server misconfigurations, authentication flaws, and injection vulnerabilities that are not visible in the source code.
- Manual Penetration Testing: While automated tools are efficient, they cannot replicate the creativity and intuition of a human attacker. Manual penetration testing involves security experts attempting to exploit the app using frameworks like the OWASP Mobile Security Testing Guide (MSTG). This is crucial for discovering complex business logic flaws and nuanced vulnerabilities that automated scanners miss.
Implementing a Continuous Security Testing Strategy
To be effective, security testing must be a continuous and integrated process, not a one-time event before release. This “Shift Left” approach embeds security into every stage of the software development lifecycle (SDLC).
- Integrate into Your CI/CD Pipeline: Automate SAST and DAST scans within your Continuous Integration/Continuous Delivery pipeline. This ensures that every code commit is automatically checked for new vulnerabilities, providing immediate feedback to developers and preventing insecure code from reaching production.
- Combine and Prioritize: Use a combination of SAST, DAST, and manual testing for the most comprehensive coverage. Implement a risk assessment framework to prioritize findings based on their severity and potential business impact, allowing your team to focus on fixing the most critical issues first.
- Conduct Regular, In-Depth Assessments: Supplement automated scanning with periodic, in-depth manual penetration tests, especially after major feature releases or infrastructure changes. For a broader view of testing beyond just security, you can reference our comprehensive mobile app testing checklist.
8. Secure Session Management and Token Handling
Secure session management ensures that once a user authenticates, their interactions remain secure, private, and continuous until they explicitly log out or the session times out. It relies heavily on the secure handling of authentication tokens, which act as temporary keys granting access to protected resources. Without robust session controls, an app is vulnerable to session hijacking, replay attacks, and unauthorized access, making this a critical checkpoint for developers.
Implementing Secure Session Management
A user’s session is a high-value target for attackers. Properly managing its lifecycle from start to finish prevents unauthorized actors from taking over a legitimate user’s account. This goes beyond simple login and logout functionality and is essential for apps like LinkedIn that maintain persistent sessions across multiple platforms.
- Enforce Server-Side Invalidation: Upon logout, password change, or other sensitive events, the session must be terminated on the server side immediately. Simply deleting the token from the device is insufficient, as a captured token could still be valid. This prevents stolen tokens from being used after a user has logged out.
- Implement Timeouts and Re-authentication: Use strict, server-enforced session timeouts for inactivity. For high-security applications, require users to re-authenticate with a password or biometrics before performing sensitive actions, even within an active session.
- Monitor for Anomalies: Track session activity to detect suspicious patterns. Flagging or terminating multiple concurrent sessions from geographically distant locations, for example, can be an effective defense against account takeover attempts. Slack’s ability to manage sessions across different devices and workspaces provides a great example of this in action.
Best Practices for Token Handling
Tokens, such as those defined by standards like JWT.io and managed by platforms like Auth0, are the linchpin of modern authentication. How they are generated, stored, and refreshed directly impacts your app’s security posture and is a core component of any comprehensive mobile app security checklist.
- Use Short-Lived Access Tokens: Access tokens should have a very short lifespan, typically minutes, not hours. This drastically limits the window of opportunity for an attacker if a token is compromised.
- Pair with Long-Lived Refresh Tokens: To avoid forcing users to log in constantly, use a separate, long-lived refresh token. This token’s sole purpose is to securely request a new access token when the old one expires. Refresh tokens must be stored with the highest level of security and should be revocable.
- Store Tokens Securely: Never store authentication tokens in insecure locations like SharedPreferences (Android) or UserDefaults (iOS). Always leverage the platform’s hardware-backed secure storage: the iOS Keychain and Android Keystore system. These mechanisms encrypt the tokens and protect them from extraction, even on a rooted or jailbroken device.
Mobile App Security Checklist Comparison
| Security Measure | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Data Encryption in Transit and at Rest | Medium to High 🔄 | Moderate; requires key management and CPU for encryption ⚡ | Strong data confidentiality and integrity 📊 | Protecting sensitive data in storage & transmission 💡 | Protects against breaches, meets compliance ⭐ |
| Secure Authentication and Authorization | High 🔄 | High; requires MFA, biometric SDKs, token management ⚡ | Reduced unauthorized access, granular control 📊 | User identity verification and access control 💡 | Significantly lowers breach risk, supports compliance ⭐ |
| Input Validation and Sanitization | Medium 🔄 | Low to Medium; mainly dev effort, client + server side ⚡ | Prevents injection and malformed input attacks 📊 | All user input handling scenarios 💡 | Prevents injection attacks and data corruption ⭐ |
| Secure Code Storage and Anti-Tampering | High 🔄 | Medium to High; obfuscation tools, runtime protection ⚡ | Protects code integrity and IP; detects tampering 📊 | Applications at risk of reverse engineering 💡 | Protects IP and prevents code modification ⭐ |
| Secure Network Communication | Medium 🔄 | Moderate; TLS setup, cert management ⚡ | Confidential, intact data in transit 📊 | API and backend mobile communication 💡 | Defends against network attacks, secures endpoints ⭐ |
| Sensitive Data Protection and Privacy | Medium to High 🔄 | Medium; data classification, consent management ⚡ | Compliance and user trust; reduced breach impact 📊 | Apps handling personal and sensitive data 💡 | Minimizes liability, builds trust, enables compliance ⭐ |
| Security Testing and Vulnerability Assessment | Medium to High 🔄 | High; tools, manual review, expertise ⚡ | Early vulnerability detection and risk reduction 📊 | Continuous security validation during development 💡 | Identifies flaws before release, improves security posture ⭐ |
| Secure Session Management and Token Handling | Medium 🔄 | Medium; token lifecycle and secure storage ⚡ | Secure user sessions; prevents session attacks 📊 | Apps with persistent login and API access 💡 | Secures auth state and scalable session handling ⭐ |
From Checklist to Culture: Embedding Security into Your App’s DNA
Navigating the extensive mobile app security checklist we have detailed is a monumental first step toward building a truly resilient application. You have explored the critical pillars, from fortifying data with robust encryption to validating every user input and securing your code against tampering. However, the greatest mistake a development team can make is viewing this checklist as a one-time task to be completed and filed away. True security is not a static achievement; it is a dynamic, continuous commitment.
The real goal is to transcend the checklist itself and foster a culture where security is an intrinsic part of your app’s DNA. It must be woven into every sprint planning meeting, every line of code, every API call, and every deployment. This cultural shift transforms security from a burdensome afterthought into a shared responsibility that empowers your team and protects your users proactively, not reactively.
Recapping the Pillars of a Resilient Security Posture
The eight core areas we covered are not isolated silos. They are deeply interconnected, forming a layered defense where the strength of one pillar reinforces the others. Think of them as a holistic system:
- Protecting Your Data: Combining strong encryption for data at rest and in transit with strict sensitive data protection protocols ensures that even if one layer is compromised, your users’ information remains unreadable and secure.
- Controlling Access: Secure authentication, authorization, and session management work in concert to verify that users are who they say they are and that they can only access the resources they are permitted to, for the duration they need to.
- Ensuring Code and Communication Integrity: Writing secure code with rigorous input validation, preventing reverse engineering through anti-tampering, and forcing all communication over secure channels like TLS creates a hardened application core that is difficult to exploit.
- Validating and Responding: Continuous security testing and vulnerability assessments are your feedback loops, confirming your defenses are working. They are essential for discovering weaknesses before malicious actors do.
Actionable Next Steps: Turning Your Checklist into a Living Strategy
With this knowledge, your journey is just beginning. To translate this checklist into a durable, long-term strategy, consider these immediate next steps:
- Conduct a Baseline Security Audit: Use this mobile app security checklist as your guide to perform a comprehensive audit of your current application. Create a prioritized backlog of security tasks, ranking vulnerabilities by potential impact and exploitability to tackle the most critical gaps first.
- Integrate Security into Your SDLC: Embrace a “Shift-Left” mentality. Introduce security requirements during the initial design phase, automate security scans (SAST and DAST) within your CI/CD pipeline, and conduct regular secure coding training for your developers. Security should be a constant, not a final gate.
- Establish a Dynamic Remediation Plan: The modern threat landscape moves too quickly for traditional release cycles. You must have a plan for how to respond to zero-day vulnerabilities. This is where your ability to deploy urgent fixes becomes a critical security function itself, bypassing the lengthy app store review process when every minute counts.
The Unseen ROI of a Security-First Culture
Investing in a robust security culture delivers returns that extend far beyond preventing a data breach. It builds unshakeable user trust, which is the ultimate currency in the digital marketplace. A reputation for security becomes a powerful brand asset and a key competitive differentiator, especially in enterprise or B2B markets where security is a non-negotiable requirement.
Furthermore, addressing security issues early in the development lifecycle is exponentially cheaper than remediating a vulnerability discovered in production. A proactive approach saves significant time, money, and reputational damage down the line. It transforms security from a cost center into a value driver that supports sustainable growth and innovation. Your commitment to this ongoing mobile app security checklist is an investment in your app’s future.
The path to comprehensive mobile app security is a marathon, not a sprint. It demands vigilance, continuous learning, and a deep-seated commitment from every member of your team. By moving from checklist to culture, you are not just building a more secure app; you are building a more resilient business and a more trustworthy brand.
A critical part of a modern security response plan is the ability to patch vulnerabilities instantly. For React Native apps, waiting for app store approval is no longer a viable option. CodePushGo empowers you to deploy encrypted, over-the-air (OTA) updates directly to your users’ devices, closing security gaps in minutes, not weeks.




